Free Trojan Remover
Home Trojan Remover Worms Cleanup Removal Contact Privacy Policy Disclaimer Disclosure
Trojan Threats & How To Remove Them

When you download free software of any kind from the internet, sometimes these files are programmed with the trojan horse infection. Trojan horse threats are malicious programs that are able to appear to the user as any other legitimate application, however, once you install the application it will infect your entire system and execute commands that will cause instability and open the door for hackers.
The Best Mini Vape Devices for Portability and Convenience
fake-watches.is: the best site to buy replica watches online. High quality watches, unbeatable prices, and fast shipping!
A lot of people tend to think that trojans are also some form of computer virus. The truth is that they are very much different although the two use similar mechanisms for attacking computers. The viruses are mostly concerned with the damaging of files in the computer, which results in instability and makes your applications run very slow. They also use up the computer memory and interfere with the system file structure. The trojan horses on the other hand interferes with the functionality of the computer after a long period of time and opens gateways for hackers. The main reason as to why a hacker may use this particular threat is because the program is able to steal very vital information from the computer of the user.
Removing The Trojan Horse Infection
Using a quality trojan remover tool that has been designed to effectively eliminate this type of malware is the best option anyone can use to rid their systems of these threats. Most commercial antivirus programs are in fact trojan remover programs because they have signature logs that enable them to detect a variety of threats apart from viruses.
There are few precautions that you as a computer user need to follow in order to ensure that you don’t get infected with a trojan:
* Never execute any file or task in your computer if you don’t trust that source
* Don’t try to open any e-mail attachments that have been sent to you unless you know who they are from.
* Be careful when downloading and installing free screensavers or other files with .exe extentions because they are notorious for containing these kinds of threats.
* Use a trusted trojan remover software and try to avoid free trojan remover tools.

There are many people who have been using trojan horse infections to carry out malicious activities such as sabotage & hacking to name a few. It is quite alarming how easily your computer can be attacked by these dangerous threats. When you get into the habit of downloading and installing free things from the internet and then using them for your own personal gains, you need to take geat caution because the internet is the most common way of getting infected with malware.
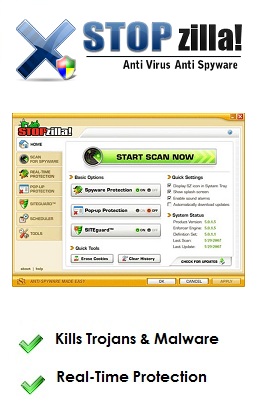
Because free software is available in large numbers, malicious programmers are able to target these free applications which are downloaded by millions all over the globe. Protect your computer with trojan remover software that comes from reputable internet security companies. We recommend StopZilla Antivirus as a quality defence against any PC infection.


- What Does Blue Razz Ice Elf Bar Taste Like?What Does Blue Razz Ice Elf Bar Taste Like? What Does Blue Razz Ice Elf Bar Taste Like? If you’ve ever wondered what a Blue Razz Ice Elf Bar tastes like, you’re not alone. This unique and delicious treat has been gaining popularity in recent years, and with good reason! The Blue Razz Ice Elf… Read more: What Does Blue Razz Ice Elf Bar Taste Like?
- The Importance of Verifying Documents and Links: A Comprehensive Guide for Reliable InformationIntroduction: Why Verification is Crucial in the Digital Age In today’s digital age, the importance of verification cannot be overstated. As information becomes increasingly accessible and abundant online, it is crucial to ensure the reliability and accuracy of the content we consume and share. Whether it is verifying documents or checking the authenticity of links,… Read more: The Importance of Verifying Documents and Links: A Comprehensive Guide for Reliable Information
- Exploring the Digital Landscape: How Technology is Shaping Our Lives and BusinessesIn today’s fast-paced world, technology has permeated every aspect of our lives, transforming the digital landscape in ways we could have never imagined. It has become a driving force that is not only shaping the way we live but also revolutionizing the way businesses operate.The rapid advancements in technology have sparked a wave of innovation,… Read more: Exploring the Digital Landscape: How Technology is Shaping Our Lives and Businesses
- Understanding the Malware Threat: How to Protect Your Devices and DataIntroduction: Defining Malware and Its Impact on Individuals and Businesses In today’s digital age, the threat of malware, computer viruses, and other cyber security threats has become more prevalent than ever before. The consequences of a data breach or the infiltration of malicious software can be devastating for individuals and businesses alike. However, with the… Read more: Understanding the Malware Threat: How to Protect Your Devices and Data
- Protect Yourself: Be Wary of Malware-Infected Files and Safeguard Your Digital SecurityIntroduction: Understanding the Threat of Malware and Its Impact on Your Digital Security In today’s digital age, the risk of malware-infected files and other digital security threats is higher than ever before. Malware poses a significant threat to individuals and businesses alike, as it can compromise sensitive data, disrupt operations, and even lead to financial… Read more: Protect Yourself: Be Wary of Malware-Infected Files and Safeguard Your Digital Security
- Unlocking New Possibilities: How “Opens Gateways” Technology is Revolutionizing Various IndustriesThe groundbreaking technology brought forth by Opens Gateways has truly revolutionized various industries, opening up limitless possibilities and paving the way for transformative advancements. With its cutting-edge solutions and innovative approach, Opens Gateways has disrupted traditional norms and reshaped the landscape of numerous sectors. Through their unparalleled expertise, they have introduced a new era of… Read more: Unlocking New Possibilities: How “Opens Gateways” Technology is Revolutionizing Various Industries
- Understanding Security Considerations and Effective Risk Mitigation Strategies: A Comprehensive GuideIntroduction: The Importance of Security Considerations and Risk Mitigation In today’s digital age, security considerations and risk mitigation strategies have become paramount for individuals and businesses alike. The ever-evolving threat landscape calls for a proactive approach to safeguarding sensitive information and mitigating potential risks. Understanding the importance of security is crucial in order to protect… Read more: Understanding Security Considerations and Effective Risk Mitigation Strategies: A Comprehensive Guide
- Revolutionizing the Retail Industry: How Technology is Reshaping the Way We ShopIn today’s fast-paced digital era, technology has become an integral part of our lives, transforming various industries, including retail. With advancements in technology, the way we shop has undergone a significant revolution. From online shopping to personalized recommendations and seamless checkout experiences, technology has reshaped the retail landscape. One of the key drivers of this… Read more: Revolutionizing the Retail Industry: How Technology is Reshaping the Way We Shop
- Stay Safe Online: Essential Tips for Identifying Suspicious Files and Links Before DownloadingIntroduction: The Growing Threat of Malicious Files and Links In today’s digital age, our online presence has become increasingly vulnerable to cyber threats. The rise of suspicious files, links, and malware poses a significant risk to our internet safety. However, with the right knowledge and tools at our disposal, we can protect ourselves from these… Read more: Stay Safe Online: Essential Tips for Identifying Suspicious Files and Links Before Downloading
